What do you think?
Rate this book


239 pages, Paperback
First published September 1, 1997
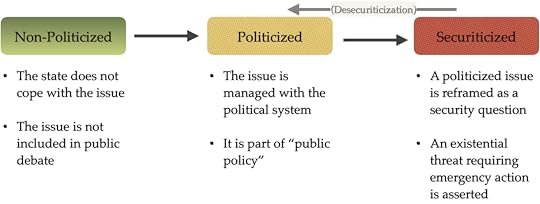
Update re the real world, June 2022. Although this book (and my review) is about the securitization process, the politicization process is of even broader interest and applicability. I recognized this while reading the New York Times article, «A Mental Health Clinic in School? No, Thanks, Says the School Board» and decided to add a small note referencing this in the comments, below.

Generally speaking, the military security concerns the two-level interplay of the armed offensive and defensive capabilities of states, and states’ perceptions of each others’ intentions. Political security concerns the organizational stability of states, systems of governments and the ideologies that give them legitimacy. Economic security concerns access to the resources, finance and markets necessary to sustain acceptable levels of welfare and state power. Societal security concerns the sustainability, within acceptable conditions for evolution, of traditional patterns of language, culture and religious and national identity and custom. Environmental security concerns the maintenance of the local and the planetary biosphere as the essential support system on which all other human enterprises depend (page 8).